For a little more than a month now, I’ve been using NextDNS, to see if it can provide another layer of protection against ads, trackers and malware. Here are my impressions.
NextDNS replaces your default DNS provider, usually your ISP, unless you’re the kind of technically savvy user who’s used to setting your DNS manually, either in your computer’s settings or in your router.
How it protects you is ingenious. As you browse to a webpage, it often includes a lot of elements that include hidden pixels or scripts that allow the advertising giants to track your interests and present ads based on the data they’ve gathered about you. Or it may include malicious scripts. These days, even going to a legitimate website can expose you to bad actors, as many of them sell advertising space with little control over who buys that ad space or what they inject into those ads.
NextDNS keeps a continuously updated database of trackers, bad actors and iffy websites, and when your computer makes a DNS query for one of those sites, it sidetracks it so that resource isn’t found. Basically sends that to a dead-end. I have yet to find any page that doesn’t load properly even with those extraneous elements blocked.
Set-up is a breeze. NextDNS provides clear, easy-to-follow instructions for Windows, macOS, Linux, ChromeOS, Android, iOS, routers and several browsers, although Vivaldi is currently not one of them. But set up your computer or router to use NextDNS and you’re set.
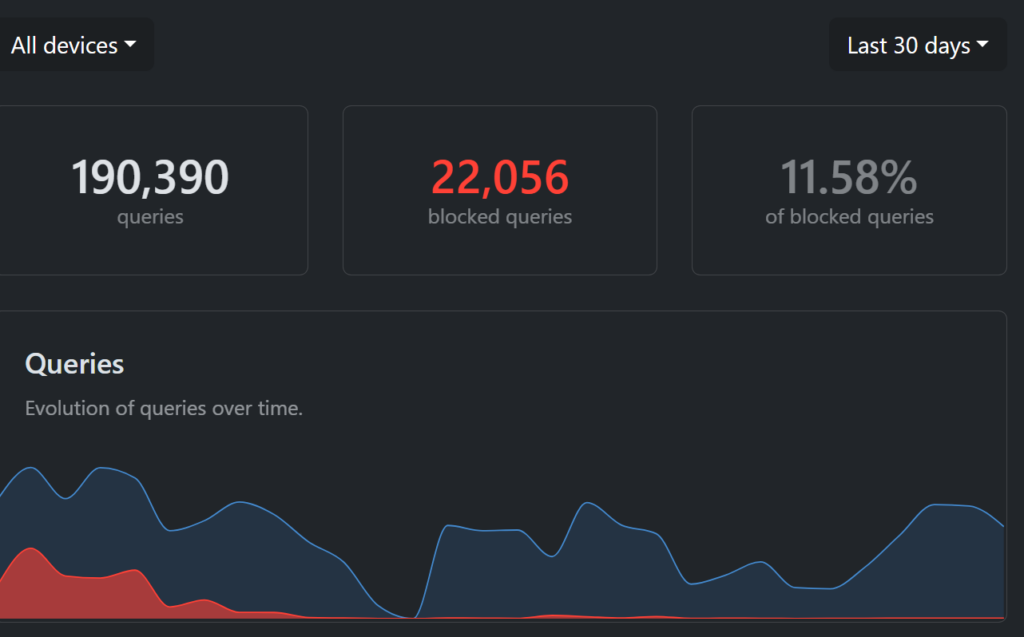
There are paid plans at very inexpensive prices, but I found that even the free plan was more than enough for me. The free plan allows up to 300,000 queries per month. Over the last 30 days, I’ve used a little more than 190,000 queries. Over time you can see the number of blocked queries decreases dramatically. That’s a result of both regular dns caching and a little hack I’ve been using.
In addition to NextDNS I’ve also been creating my own local blocklist by checking my NextDNS logs and adding the trackers’ domains to my local hostfile with a loopback entry. I’ll detail that further in a future blog post.
One use case I’m very excited about is using this for family members. If you’ve read this far, I’m guessing you’re the default IT person for your family and friends. By setting up NextDNS as your mom’s DNS service, you’ll ensure that she won’t accidentally become a victim of a scam when she automatically clicks on that first link in a Google search. I can tell you, trying to explain sponsored placement in a Google search to a 90 year old is a lot more work than setting up NextDNS for my in-laws was.
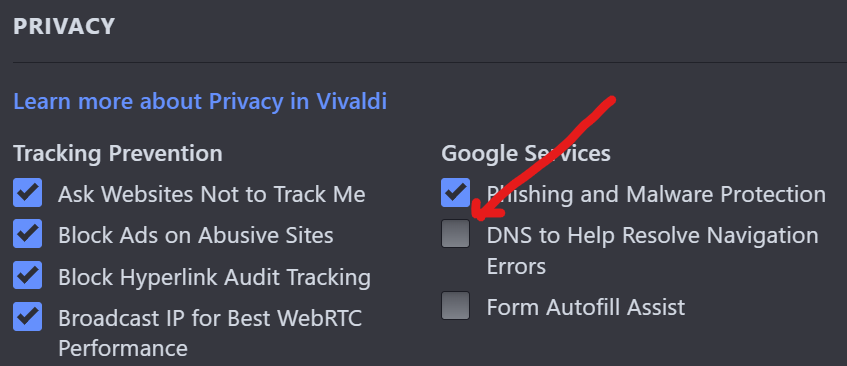
One caveat for my fellow Vivaldi users. Vivaldi’s wonderful privacy and security settings are pretty granular, but if you’re going to use NextDNS as an additional layer of security, there’s one thing you’ll want to disable. In the Privacy and Security Settings, look under “Google Settings” and uncheck DNS to help resolve Navigation Errors. You want to let NextDNS do your DNS resolution.
So what do you think? If you’re curious about NextDNS check out their website. Give it a try and let me know what your experience is. If you have other tips for foiling bad actors online, I’d love to hear about it in the comments!